Browse our resources to explore the current best practices for validating storing and handling biological materials and how these techniques support data integrity and reproducibility.
Cell line authentication slideshare.
While naming the cell lines it is absolutely necessary to ensure that each cell line designation is unique so that there occurs no confusion when reports are given in literature.
March 2015 isoenzyme analysis has been withdrawn until further notice.
Atcc is committed to improving the authentication of cell lines and microbial cultures.
Avoidance and denial behaviors are widespread say researchers interviewed by nature methods.
Further the results can vary depending on the history of the cell line and the type of media used for cell growth.
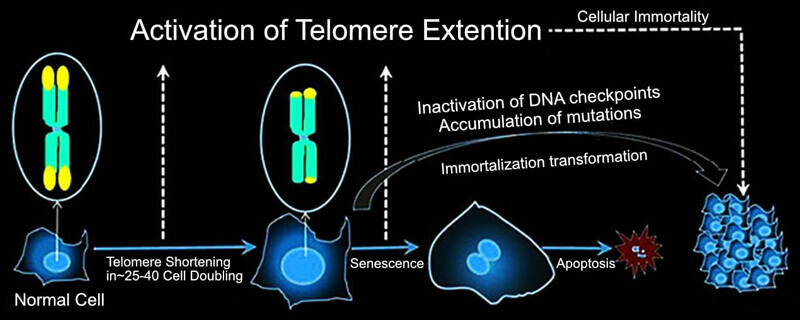
An immortalized or continuous cell line has acquired the ability to proliferate indefinitely either through genetic mutations or artificial modifications.
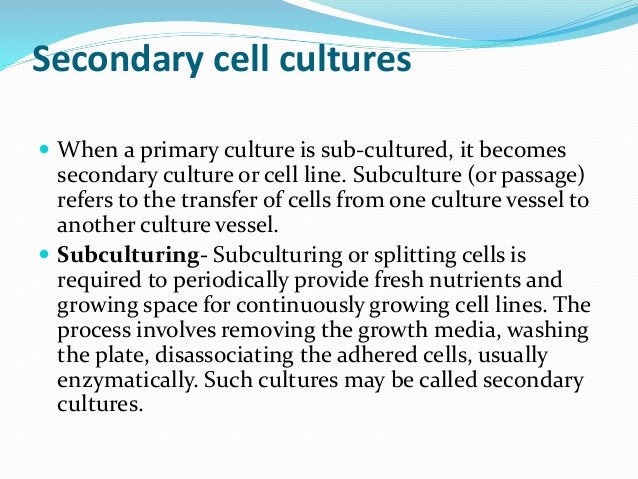
Cell lines cells that have been continually passaged over a long period of time and have acquired homogenous genotypic and phenotypic characteristics.
Animal cell culture and characterization of cell lines by cell morphology chromosome number banding and karyotyping etc.
Our current clients include pharmaceutical and biotechnology companies universities cancer centers research hospitals and more.
Authentication i e confirmation that the cell line is not cross contaminated or misidentified confirmation of the species of origin correlation with the tissue of origin which.
Cell line authentication can seem too time consuming or daunting.
Using standardized techniques authentication enables communication among all users about the resource and ensures valid reproducible experimental results.
Authentication of a cell line is the sum of the process by which a line s identity is verified and shown to be free of contamination from other cell lines and microbes.
For instance the code nhb 2 1 represents the cell line from normal human brain followed by cell strain or cell line number 2 and clone number 1.
We suggest consulting with one of our experts to determine the best methods for using rapd for cell line authentication that are suited for your needs.
They understand why their colleagues.
Further at the.
Do not include plans for the development and authentication of new key biological and or chemical resources such as a new human cancer cell line or a new antibody.
Applicants proposing to generate a new key biological and or chemical resource must describe the development and authentication of the resource in the approach section of the.
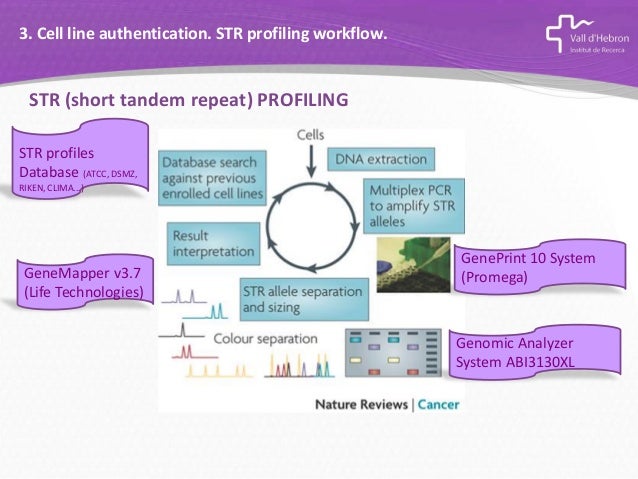
The geneprint 10 system provides a convenient str based method for cell line identity confirmation and for detection of intraspecies contamination in cultured human cell lines.